2.1 KiB
2.1 KiB
giftwrapping
Flag
HTB{upx_41nt_50_h4rd!!}
How to solve
- The binary is packed using the upx packer
- It first needs to be unpacked in order to reverse engineer its contents
- Fortunately
upxis open source and rather well documented- unpack using:
upx -d gitfwrap
- unpack using:
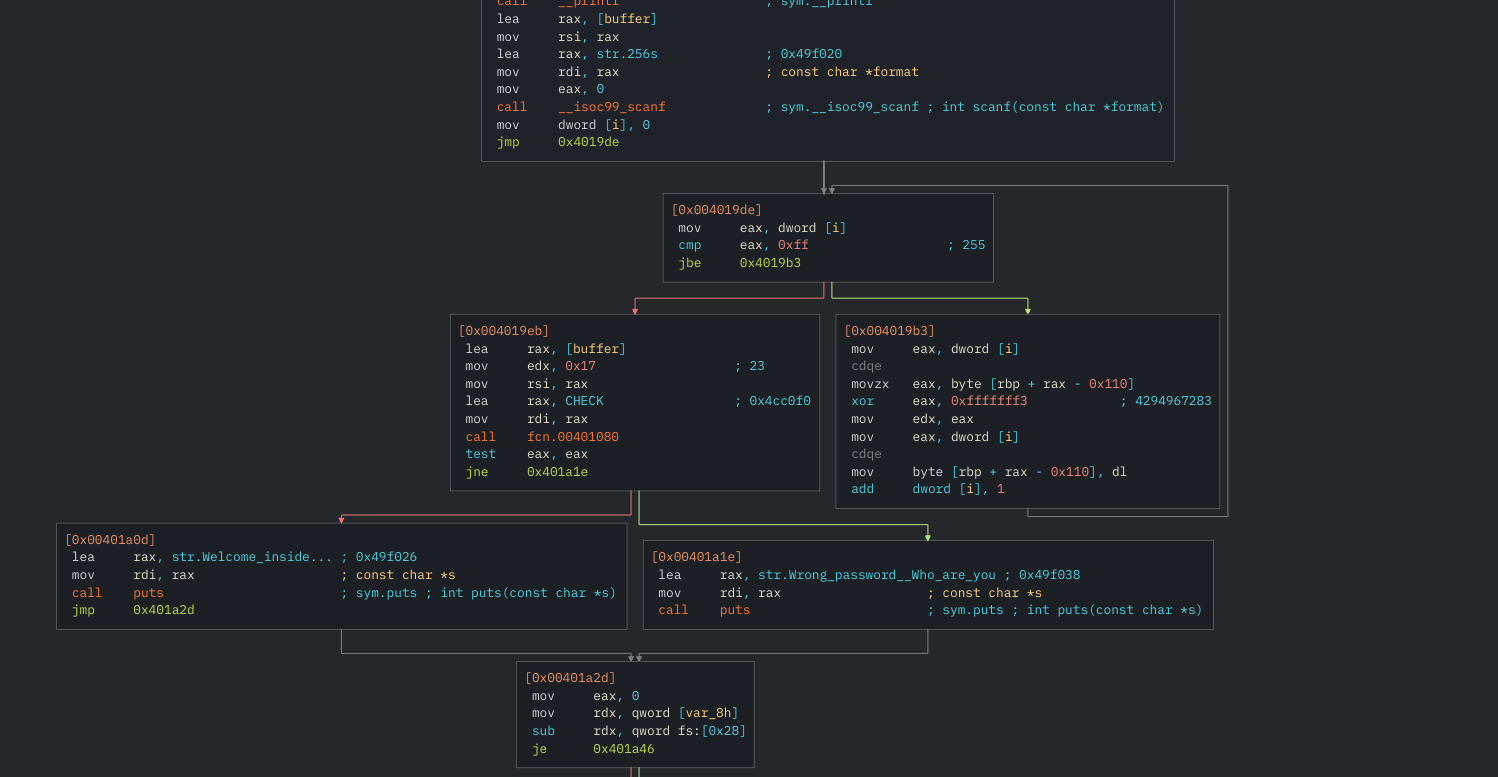
- Fire up radare2/cutter and disassemble the binary
- The program logic is a bit confusing due to the unpacker doing weird stuff
- After the call to
scanfthe programm enters a loop where some data fromrbp+rax-0x110gets loaded intoeax - Then the data gets xored bytewise with
0xffffff3 - Once this is done for all bytes the program moves to a check section
- There a function call to
fcn.00401080is made. - Don't bother, this is no password check, it's just an implementation of memcompare
memcmpfrom the c++ lib - If the data matches the welcome message is shown
- So the flag needs to be somewhere in the data that gets xored.
-
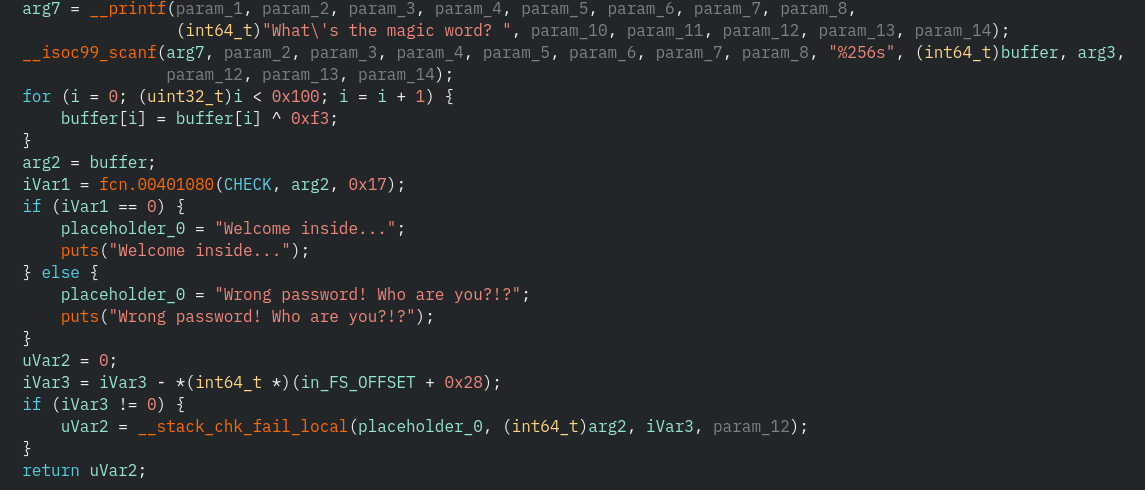
Once I was able to install the ghidra decompilation plugin for radare2 the process gets clearer.
-
Ghidra does a great job decompiling the xor mechanism
-
Don't be confused about the loop condition
i < 0x100- Yes, the code should loop over
0xff bytes. - But since there is a
<it's all okay ;)
- Yes, the code should loop over
-
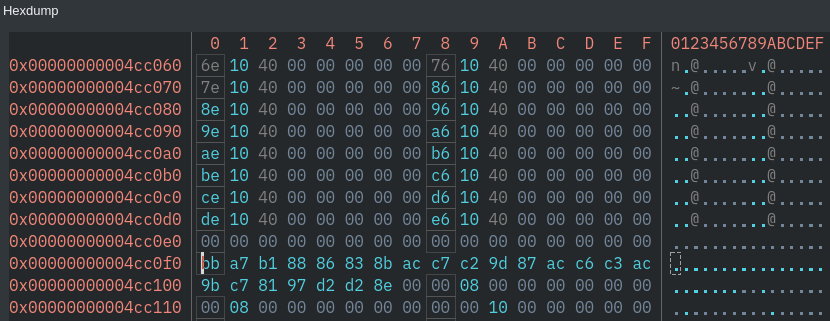
Time to grab the data using
gdband convert it to a string
- don't forget to set you disassembly flavor to intel
- load the program
gdb ./giftwrap - set a breakpoint at the desired movzx instruction
break *0x004019bb - run until break
r - get the start address which is being loaded using
print $rbp + $rax - 0x110which is0x004cc0f0 - print the bytes at this address or simply navigate to it using the hexdump tool
- Now copy all this data and convert it to ascii using some python
b'\xbb\xa7\xb1\x88\x86\x83\x8b\xac\xc7\xc2\x9d\x87\xac\xc6\xc3\xac\x9b\xc7\x81\x97\xd2\xd2\x8e'
out = []
for i in range(len(buf)):
out.append(chr(buf[i] ^ 0xf3))
print(''.join(out))